RPCSniffer
RPCSniffer sniffs RPC messages in a given RPC server process.
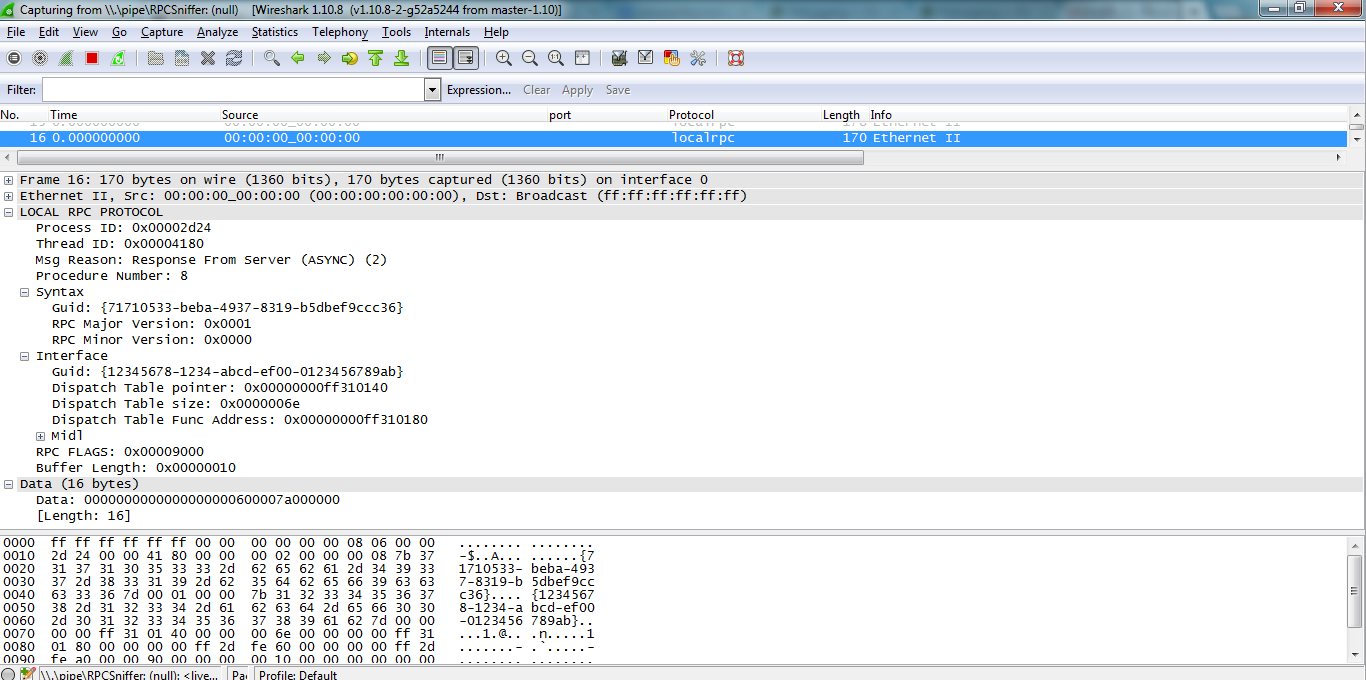
General Information
With RPCSniffer you can explore RPC Messages that present on Microsoft system. The data given for each RPC message contains the following details:
- Type (Async/Sync , Request/Response)
- Process number
- Thread number
- Procedure number
- Transfer Info
- GUID
- RPC minor version
- RPC major version
- Interface Info
- GUID
- Dispatch table pointer
- Dispatch table size
- Dispatch table function pointer
- Midl Info
- Dispatch pointer
- Server function address
- RPC Flags
- RPC Data
Install steps
Install python 2.7 (64 bit)
Install the latest Winappdbg python package
Install Wireshark
Intsall the latest Pyreshark python module for wireshark
grab the file "pyreshark_rpc_dissector/rpc_protocol.py" to "c:\Program Files\Wireshark\python\protocols\"
Run
- Start Wireshark from cmd and prepare it to use rpcsniffer's pipe
"C:\Program Files\Wireshark\Wireshark.exe" -i \\.\pipe\RPCSniffer
- Run python main.py with the server process to listen
python main.py --help
usage: main.py [-h] (-p PID | -n PROCNAME)
main.py: error: one of the arguments -p/--pid -n/--procname is required
- go back to wireshark and click "start"
- from now you'll get all rpc messages in wireshark
Implementation
Check the wiki for more info.
TODO
This project is a POC for now, but you can help me add some stunning features that will allow us to really understand RPC internals.
- Dissect the rpc raw data (maybe by using the RPCView decompiler and find a MIDL-dissector?)
- Integrate it with the wireshark midl-dissector itself
- Retreive more data from the rpc message (I used REACTOS to parse the RPC MESSAGE). Can you find more usefull data from this windows struct?
Anyway, I'd be more than happy to receive bug reports, suggestions and anything else.
Some Comments
- It's very usefull to use the powerful and free tool called RPCView for finding interesting RPC server processes, decompile its interfaces and more. Take a look at http://rpcview.org/index.html